
What are the top Application Modernization Strategies for Your Business
Modern programs communicate with other apps through microservices and APIs, established systems required entire development team for even the basic third-party connection. Therefore, organizations felt the requirements for a swap and that is what the rise of application modernization brought with it.

Application Modernization defination
The process of emending, modifying, or integrating current applications to better align them with current business condition and market rivalry is known as application modernization. Applications may be updated by migrating them to a newer platform.
Upgrading their mechanization stacks and build, or just integrating new functionalities with advanced technologies.
List of Businesses must think about Application Modernization
SaaS Companies
Companies that engages software to bring a service are known as SaaS enterprises. The product is developed, hosted, and updated in-house by these organizations. To remain their service or product in running, many SaaS enterprises need the help of complete in-house development team. As a result, azure app modernization is critical to the long-lived feasibility of firms like these.
Companies with In-House Developers
It is possible that few companies do not follow the SaaS model. They still need a team of developers to carry on to provide value to their customers or thrive in a trade where customers want access to mobile apps. As an outcome, they must also think about azure apps modernization as a method to keep upgrading their services.
Methods for a triumphant Application Modernization Strategy
Understand Your Applications
Companies must first recognize their point from where they begin before they can start to modify their applications. A standard measurement should be taken to get a judgment of how well an company's applications are working. Using this judgments, companies may recognize and prioritize the optimal strategy for application modernization for each software.
Through the use of numeric measurements, businesses can collect data on the attributes of individual applications. Having a comprehensive and objective view of an application helps organization make better decisions on how to upgrade the application.
Illustrating the motive of Modernization
Key part of application modernization is featuring out what company want to achive with new application. "What business and technological improvements do you point to achieve with the application modernization?"
Answer to this question will grant for a more accurate execution strategy. The next step is to create and apply a prioritization set up that will accommodate in the creation of a modernization schedule.
How To Choose Right Technology
Your distinctive selling theory may be enhanced by incorporating advanced technologies into your company offerings. Organization must keep up with the newest technologies, but they should also make sure that the solution they select is suitable for their specific use case
What are the Implementation and Continuing Support
It is critical to locate a premium on a extensive data transfer plan throughout the deployment and implementation phases to keep away from duplication, inconsistent data, security breaches, or unauthorized an unofficial access. An easy transformaiton may ensure the security of a company's data carried out by data migration pro using an progressive approach.
By taking a complete approach to modernization, you may enhance team and customer experiences, raising revenue, and remove techno-managerial defects that result in time and resource waste.
Outline
Legacy methodology and practices can not meet ongoing business KPIs since they are ineffective, time-consuming, and costly. There needs to be a structured, bit by bit plan of action for application modernization. Thus, there will be less difficulties and more time for end-users to become familiar an easier with the new application.

Advantages of Email Marketing in Business establishment
There are many of wrangle around whether email marketing works or not. Here are some points discussed how email marketing is advantageous for business startups and why business should choose for mass email services.

Email marketing is the affordable choice at hand if we estimate it with any other digital marketing method. There are numerous bulk email service provider available in the market which allow you to send 8,000 to 12,000 emails for just $10 to $15.
You may use your existing consumer database with another database if you are obtaining one for utilizing them in email marketing. Only make sure you don’t spam customers by frequently sending them unnecessary emails.
Email Marketing’s Return on investment is one step ahead:
Numerous substantial advertising services and email marketing companies have concluded in their research that email marketing is clever to bring lofty Return on investment than any other marketing strategy. But it also has to be finished in a suitable method in order to obtain that Return on Investment. More of the new generation choose email over anything for receiving business communication. Business to Business email operations receive big gain. This marketing strategy can be utilized to generate leads, increase traffic and brand recognition. Because of the above mentioned points, email marketing is clever to give a higher return on investment.
Owner Have Full Control on it:
In this email marketing method, if you have a quality database that is collected through your customers and with efforts in gathering the email from users then you can give size-able benefits from that database. Be it third party or paid advertisements you will have to invest in to make the message reach the customer every time. But that is not with email marketing, if the strategist have a good IP and database they can reach their customer whenever they want. They can up-sell product or service, send announcements of new product arrivals and new offers. They will not require to spend every time to send email to the same customer they have addressed before.
Builds Trade Name Recall standard:
Because of most email service provider's strict email filtration, it has became hard to make Marketer's email reach to the customers inbox. Trade names whose emails successfully reach to the inbox are clever to rise their Trade Name recall value in their audience’s mind. Though it’s hard to make emails land in the inbox, if strategist able to do so, customer will know your brand and would result in establishing an ultimate trade name in the market. Depending on the email content, words mentioned in the subject line and how is your IP’s recognition all this contributes to whether email will drop to the inbox or not.
Practical segment of The Topic:
Emails can play the principal role in building your chances to reach the audience. New establishments can use the emails they are receiving from submissions to send them offers or announcements. This can lead to rise in sales and finally loftier return on investment on your email marketing efforts. This method can be a useful asset for B2B companies to transform their ideas into growth driven business.

From Small Enterprise Workstation to The Large Organizations VoIP Phone System is the Perfect Solution
This is the era of email, messaging, and video conferencing, therefore to run successful business in the competitive market, either it is small business or large organization it require a genuine phone system.

Voice over internet protocol is one of the best technologies in today’s age. Since it transmits voice calls as data over the internet rather than using phone lines. It provides numerous ultra-modern services that already contain structured landline factors. Far from the traditional fashion, VoIP phones are reasonable, genuine and expandable, and because of this, many small companies are transitioning to small business VoIP phone solutions.
As a business phone system what are the Importance of Voice over Internet Protocol
On account of the developing market of telecommunication, it has become hard to neglect the necessary enhancement of business phone systems and how these modern technologies are changing the method we work and communicate. In today's framework, VoIP is the pillar of business communication as the VoIP business phone set-up can make and receive calls over the internet, that is why it is considered one of the crucial services for small to large businesses.
Crucial advantages of Operating Small enterprise VoIP system in workstation
A VoIP service offer has various advantages to small enterprises that help them expand and thrive in the market. A common myth about Voice over Internet Protocol that it is only for large organizations.
So, let’s break this misunderstanding about VoIP phones through this blog and focus at its advantages for small enterprises.
1. Strengthened Call quality standard: To make a business gainful, organizations need to establish successful communication with their associates, clients and teams. Voice over Internet Protocol is popular for its rich calling characteristics, as long as a business has a hi-speed internet connection, this technology will execute its functionalities well.
2. Provide pliability: It provide significant pliability compared to regular phone lines. VoIP furnish workplace flexibility to users by reinforcing the BYOD (Bring Your Own Device) system, which remote employees greatly acknowledge. Besides ‘BYOD’ downloading VoIP applications helps users to scale up their work on other devices too.
3. Boost up customer experience: Voice over Internet Protocol offers ultra-modern properties like a virtual attendant or auto receptionist enable clients to connect with organization's right person right away. Additionally, it also enables a ‘Music while you are on hold’ function that engages clients at period of call hold.
4. VoIP Cloud-based integration: The integration of cloud-based services in phone system help business to increase productivity, security and effectiveness. VoIP services interface with several office technologies like voicemail, live chat, Voice and video conferencing tools, CRM platforms.
5. Simple to implement: VoIP service is easy-to-use, flexible and easy to administer. This VoIP phone technology also stamp out the need for service tech. After all Voice over Internet Protocol is a cloud-based technology, it means VoIP does not need any hardware installation on the work places.
Outline: As we have seen the above advantages undoubtedly prove that Voice over Internet Protocol phone system are a inexpensive and well founded alternative of traditional phone for start-up and small businesses.
Top trends in Web Development for upcoming year (2022)
The operation of web-development or website development involves the work of developing a Web-site for the “Internet” (The Internet is a globally-connected network) or “Intranet” (a local or restricted network within an organization).

It can vary from developing a user-friendly static page integrated with plain text to multiplex web applications, fundamentally built electronic businesses, and social network projects. The contemporary world demands organizations and entrepreneurs to stay upgraded with the modern tech-world to solve complex troubles and stay forward of their contenders. Latest technologies are poping-up every day which make the work trouble-free and increase customer engagement with its modernize User Experience (UX).
Hence, it is all-important to build latest web-tech solutions regarding SaaS applications, an online marketplace, or a fully-functional software application to stay top-driven in the market.
If you are planing to build a triumphant and viable web-tech solution so Deploy the below-mentioned top recent trends in web development for upcoming years to rise engagement and expand your business.
1. Mobile-friendly website
2. Single-page applications
3. Motion UI
4. Progressive web application
5. Voice search
6. Server-less architecture
7. Artificial intelligence (AI) and bots
8. Internet of Things (IoT)
9. Block-chain technology
From 2022, the series of web development requires to stay aligned with the latest technological trends. To remodel the way of business is conducted with their client has a lot to play to determine the victory of your directorial goal. Therefore, implementing the above-mentioned top trends and technologies can help you stay competitive and deliver a greater user experience.
MetaProton® Technologies will be delighted to transfigure your objectives into reality and enhance your business, A well grounded software engineering partner to help you implement these latest tech-trends.

Four Leading Information Technology Reinforcement Strategies in 2021-22
In terms of Information Technology Reinforcement, the global pandemic turned 2020 a year in unparalleled change that effected Information Technology service's function and business requirements. In many ways, 2020 year has allowed the corporate Information Technology division and the Tech Support in organization, in certain, to reassert their profit to the organization and its employees.

The Information Technology service team has aided with the relocation of office employee to remote functioning, playing a censorious part in company's business progression responses to the pandemic. It was noble to see that many Information Technology service helpline were an essential part of organizational resilience during year 2020. However, what are the top strategy we are going to see in 2021-22? Let's go through it.
Information Technology service helpline development and optimization will be fault-finding to IT support success:
Given the functioning and commercial crash of the global pandemic on organizations, there's a requirement for enlargement and optimization. Not only to change the conventional methods of working associated to Information Technology service distribution and support but also to reflect the need for finer, turbo, and affordable Information Technology support functions and results. This makes the essential improvement more than cost reduction and efficiency. Thanks to their remote working, employees have a size-able dependency on technology that steadily works when required. Vice versa true for customer assistance – from customer acquisition to ongoing assistance.
Digital progress will be restoring manual operations:
The distributed working arrangements caused by the pandemic have showed up the various failures of the present manually-reliant methods of business functions – such as human resources, finance, and facilities. As a result, there will continue to be lofty growth in service management potentials and the corporate Information Technology Service Management tool used to transform trade function operations and result across the organization digitally. Crucially, it is not only the technology but also associated to people and process best practices too.
Employee experience will operate Information Technology service desk change:
The value of employee experience in Information Technology support in many company has constantly grown over the last four years. And now that this year's focus has centered on the significance of employee productivity, it placed skillfully with the requirement to upgrade IT service desk operations and after-effects. Hence, Information Technology help desk development efforts will also focus on employee productivity and the dynamic employee experience. In certain, understanding that simply being economical will not work for an employee foundation. They need extra superior service experience in consumer-world interactivity and more dependent on technology accessibility at work than ever.
Information Technologies support's evaluation requires illustration and demonstration:
Value illustration and demonstration have long been hard for Information Technology division. But just because it is hard does not mean it can be pass over or ignored. For example, if an IT issue is fixed, but the affected employees or customers still can not do what they want to do, then where's the gain? Alternatively, look for your service desk's worth in terms of trade-related advantage such as - End users are extreme productive, and consumer can consistently engage with your establishment when they want, how they want, and wherever they wish, and corporate back-office operations work constructively. So the unfavorable crash of technology-related issues on business functioning and after-effect is minimized.

Disaster Recovery Objectives and their Factors
Information Technology Disaster Recovery Arrangement helps in successful recovery mainly in occurrence of unpredicted circumstance and server crash.
As organizations depend more on ultra-modern technology as well as electronic data for leading regular functioning, the significant amount of data that can be vanished with disasters take place to be abundantly rise. Undertaking a risky or course of action are approximated to lose track of high income gain and may experience increased expenses because of disasters every year. It further leads to failure, degraded trade performance, and dropping of productivity. Thus, it becomes very crucial to prevent disaster event to the possible area and further be ready with top-level recovery programs. Evaluate for dealing with the aftermath of disaster through considering Information Technology disaster recovery groundwork.
The foremost method to deal with disaster is by fabricating and administrating DRP or disaster recovery plan. The DRP must be efficient enough to get to grip every type of disaster regardless of the size of the destruction. Hence, it is extremely crucial to keep disaster recovery plans uncomplicated to follow, most comprehensible and flexible to manage with varying needs. Let’s go through the common components that must be present in DRP for successful recovery:
Build a Team for Disaster Recovery Plan:
The duty of the recovery team is to develop and maintain the DRP. A disaster recovery plan must classify the team members and render the distinct duty of each team member. Moreover, it should carry the characteristic of the person to be reached in the event of a disaster. All the team members must be well informed about the disaster and responsibilities as soon as workable for dealing with the circumstances in least time.
Pick out & Evaluate Disaster Risks and Threats:
The dedicated disaster recovery team must be able to spot and pick out the related risks and threats of the organization's IT infrastructure. This stage include natural disasters, certain man-made emergencies, and interconnected events. The disaster recovery plan will help the members of the team in the identification of the recovery master plan in addition to essets and resources. The DRP should be pre-established and must be expert to offer a well grounded solution in an defensible time frame.
Find out the Essential Applications, Records & Resources:
At first, the business has to carry forward an assessment process to find out the critical business operations. The DR plan should very focus on short-term survivability, including cash flows as well as earning. Short-term objectives are more successful than long-term ideas as they help re-establish the venture’s complete functioning ability. Although, the business must recognize the plan of action that should never be set back, such as payroll alter.
Off-site Storage operation and Backup Strategy:
This method helps in recognizing the data that must be backed up and the time frame of backup. The team responsible for carrying out backups, location, weekly or monthly backups, all must be available in the DRP. You have to make sure that the necessary applications, IT equipment, and critical record are periodically backed up. Not at all skip backing financial statements, income tax returns, employee lists, contact info, inventory records, and vendor listings.
DRP Testing and its Maintenance:
Getting a disaster recovery plan is not sufficient; you have to confirm it works correctly. Consistently carry out an initial scan to understand how effectively it works, and it is extremely important to maintain DRP. Also, if needed, upgrade the objective as per changing IT infrastructure and resources.
In synopsis, an organization must expand a DR crew for building, maintaining, implementing a DRP. Recovery plans help out to carry on with directorial work in least time after a crash. The concerned individual must update, test and keep DRP as per changing fundamentals.

The importance of Remote Infrastructure Management and why it is effective for companies, mainly during this Covid-19 Era.
Remote infrastructure management is a successful way to decrease IT expenditure. Certified RIMS providers take total authority for keeping and maintaining IT infrastructure.

Directing an on-site IT infrastructure and set-up is a tramautic operation. Dusty server room, hiring IT professional, interval to intervals maintenance are many of the functions that can deflect your mind from your real business objectives. Executing Remote Infrastructure Management can take these difficulties out. Remote Infrastructure Management is the process of directing the IT infrastructure of a company or an
organization like hardware, software, and storage devices fully or in segments from a remote location. It so happens that the whole physical infrastructure is geographically partitioned from the control of the IT services.
For organizations scattered over numerous geographical places all over the globe, it is a very difficult job to unify the monitoring and maintenance of company's IT infrastructure. It is truly beneficial in this condition because it can really support all your IT systems all over these locations centrally. It also put forward a much higher degree of supervision and maintenance. You can smoothly coordinate the operating and testing of the IT machines and systems if they’re interconnected and linked together.
How Remote Infrastructure Management is valuable for businesses and organizations? With all the below mentioned features, RIM helps organizations.
Boosted Uptime:
The top Remote Infrastructure Management service providers supply ultra-modern facilites and services to companies like finer band-width, best-quality connectivity, sizeable automation, good-standard equipment, highly skilled and expert tech team, and a wider span of other services that gain the organizations with amplified uptime.
Economising and Cutbacks:
The price involved in outsourcing company's IT tasks to a well founded RIM service provider is lesser than the cost of maintaining an on-site IT division, especially when the business locations are scattered over various geographical region and different time-zones.
All 24/7 tech support:
Flawless continuity of your organization operation is a must but IT infrastructures are open to failure and malfunctioning, so IT infrastructure need a solution that is 24×7 accessible. Remote Infrastructure Management Services provides an well organized solution by deploying a genius team that guarantee monitoring your IT infrastructure around the clock backing.
Takes the burden out of leading on-site IT assets and resources:
Remote Infrastructure Management services decreases your dependency on your on-site IT assets, this means that you can aim on your business strategies and objectives, authorizing them to focus on the maintenance of your IT infrastructure.
Turning on remote infrastructure management services can help companies in decreasing their entire risks while upgrading user satisfaction levels and quality. Anyhow, it is essential to get these services only from the formost Remote infrastructure management companies having worldwide recognized certified specialists who have multiple years of experience in providing the flawless running of the IT infrastructure of companies and organizations with continual monitoring.
Functions of Intellectual Property (The Patent Registration) in Robotics Technology.
From the year 2007, the number of granted AI and robot patents has increased globally. Here's where the part of Intellectual Property in AI, Robotics and Engineering comes into play.
Preface
These days when you speak about robotics or artificial intelligence (AI), the first element that occur to mind is ultramodern, advanced technology thursting and remodeling the planet. It’s possible to metamorphose countless, if not all aspects of human lives are giant, from the markets to hospitals to schools to your own personal kitchen.
But, AI and robotics technology is not a new idea. It has been in life and has acted a part in particular industries like manufacturing and automotive business units. It has only been in recent years with new science and technology innovations, and fields of examinations & research blended with AI and robotics that the plan of having an ultra-modern robotics technology that has much greater potential has inclined
Robots have now turned completely self-sufficient and integrated with Artificial Intelligence. They are invented with the capability to manage and resolve without human interference and judgement.
Robotics Technology and how it works?
Artificial Intelligence is the brainchild of science and technology. It covers the entirety of developing an automated bot from the design abstraction to its construction, functioning, and implementation. These robots are developed to have the potential to read and recognize their surroundings and balance their measures to achieve an objective.
The Effect of Artificial Intelligence Technology
Remodelling and Innovations in the AI field are getting modern, and it is happening at a lightning speed. It leads science fiction into actual life. It is very colletive, research in-depth, and is getting more and more compounded. With the number of human actions requiring its use growing over the decades, No surprise that the requirement for innovations and inventions in the area of AI and robotics are high.
With the variety of possible applications of this technology, it means that customer can await to obtain an extensive scale of AI and robotics-related productions, from healthcare to all industry sectors. It engages a key role in taking out jobs that may be considered too unsafe to mankind or helping human beings with finite strength.
The Intellectual Property in AI and Robotics
With the acceleration of robotics technology gaining strength over the last decade, innovators and developers are now not only facing conventional technical challenges but also they finding themselves facing competitions at a much giant and complex degree. This is where the part of Intellectual Property and patent registration comes onto the ground.
From the year 2007, there has been a climb in the number of granted robot and AI patents published globally. This is demonstration of the reality that there is a huge rise in research and development in the field of AI and robotics. And with this extensive growth comes the sizable requirement to safeguard and protect innovations and technology.
Conclusion
Owning a strong intellectual property (IP) (patent regisration) portfolio produce various advantages and trump cards for individuals to big empires. With IP rights in position, the robotics and AI company has a superior dominance of placing themselves with potential investors and industrialist. It is also clever to protect and defend competitive threats and dangers, build a well founded brand name and trademark, and safeguard the company from intellectual property theft. As technology carry on with, it is expected that the demand for intellectual property protection will rise.

Cybersecurity Figures, Foretells, and their Fixes for 2021
In 2020, Cybersecurity has sets of more dominant than ever for various domains of businesses all over the world. Numerous statistics circulated over the media, we can plainly see that no one is immune against cyber-attacks, Big contenders and many individuals investing largely in their empire's cybersecurity.
"The unwell known pandemic" unquestionably left a giant hit on the whole cybersecurity situation.
First, the worldwide lockdown forced countless companies to move to remote work. And cybercriminals took the advantage of vulnerable networks of employee's home. Numerous companies and organizations encountered data breaches at the start of the work-from-home transfer.
More than 85% of companies reported an increment in cyberattacks during 2020. The majority of the malware was received from email (More than 94% of cases) At the start of April 2020, Google notified it was blocking daily 18 million of malware e-mails associated to Pandemic. During January and April 2020, the attacks on cloud services raised by more than 610%
By all accounts, the healthcare, financial and lot more other industries were the most affected one, as they trade in with giant number of personal data.
Many investigations shows:
In year 2020, more than 25% of most cyberattacks targeted healthcare, financial and some other sectors from the starting of February month to end of April 2020, attacks against the banks rose by more than 235%. Many of the financial organizations revealed that it was much more challenging to fight against cybercriminals, as they turned much more sophisticated and civilized.
2020 has surely been an excellent year for online traders. Even though according to surveys, Pandemic has bring about large shipping hold ups for more than 35% of shoppers, the worldwide lockdown made 56% of buyers trying a new retailer throughout the Covid-19 interval. In addition, absolutely, this was the largest vacation season in the e-commerce saga.
On the other side of the coin, more online sales result in greater cyber-attacks. Of course, the e-commerce platforms have already been established adapting to the present condition, but the attackers apparently took benefit mostly at the starting of the lockdown period, initiating an exceptional number of attacks, intending to steal the consumer's data, and making unapproved transactions. Such attacks involve credit card frauds, malware, phishing attacks, etc.
Nevertheless the organizations are trying to adjust to the growing threats arriving from cybercriminals, cybersecurity experts are not confident at all, as their investigations indicate that cybercriminals are interchanging their way of actions even more, and are not intending to set back.
Here are just some number of figures and predictions for 2021, showed by Cybersecurity Ventures:
By the year 2021, Cybercrime is anticipated to cost the world around $6 trillion annually (more than double compared to the year 2015), building it the world’s third-largest economy, after the USA and China The cybersecurity specialists foretell a cyberattack event to occur in every 11 seconds in 2021 (4 times double than in year 2016) In year 2021, 1st position in the nomination “The Quickest Multiplying type Of Cyber-crime” will go to Ransomware. As the global costs bring about by such type of destruction will extend more than $19.5 billion (56 times greater than in 2015).
Proceeding into account all the specified statistics and forecasts, it is clear that companies and individuals must rework entirely on their cybersecurity perspectives and game plans. So what can we all do to outlast the cybercrimes much more functionally and successfully?
Enable your hired hands with Knowledge and understanding
It has been demonstrated that more than 88% of cyber-attacks are interconnected to human errors. Frequently, Individuals take cybersecurity for granted, and many of the employees are not even up to date and clued up of cyber-attack catagory type and dangers until it is too late. Any employee, who is not knowledgeable about cybersecurity, can unwillingly fall victim to cyber-attacks, puting down your organizaton and clients at risk of this danger. That’s why it is very important to instruct and educate the employees, mainly for todays when lot of them are operating their work from home.
So start unrolling cybersecurity education and awareness immediately: furnish your employees with all the mandatory and essential information in regards to cyber threats and terrible outcomes and consequences led by those marshal cybersecurity training conferences and phishing experiments or trials. Stay in power of the action: make your employees use only secure applications and strong passwords, describe them why they should get the concent of the IT team before installing any of the applications and softwares, and why they might have finite access to some data, in some cases.
Protect and Defend the organization Proactively and Dynamicaly
Protecting your system from any vandalization or harm is always superior than restoring it. These cyber-criminals will always hunt for the flaws and weak points in your organization’s cybersecurity infrastructure, that is why you consistently have to be one step ahead of their strategy and detecting a cyber-attack before it take place. This method of plan will help you to minimize the harm and it will keep your infrastructure away from major troubles. Take all the required safeguards to make sure your data is secured.
Do you have any Backup Plans?
Many investigations and researches shows that most organizations didn’t plan about their infrastructure's back-up and strategy in case the cyber-attackers have succeeded to loot the data.
Once again, Train and upskill your employees: From individuals to organizations everyone must be up to date of their own responsibilities in all the possible outlines Always control and keep an eye on the total data stored and shared in and out side your organization's network. Although the cyber-attacks on cloud storage have rise extremely, always remember to back up your whole project.
Nevertheless how to ensure that the data stored on your servers, computers and cloud services is truly secured even if it was thieved? The solution is easy. Make it useless for the cyber criminals!
As we have seen, all the following information write above, your data is extremely protected not when it cannot be breached (because it always can), but when it must not be readable by prohibited users and cyber attackers.
Robotic Process Automation (RPA) An ultimate Automation Testing Tool in AI industry.
Robotic Process Automation is the upcomming tomorrow of automation testing tool, which performs a very essential part in Application testing process to get rid of the reappearing manual code execution.
Robotic Process Automation (RPA)?
It is an Application Testing technology where business prosidure can be put in artificial intelligence technology and directing a machine or robot to perform repetitive guided jobs. The robot in RPA are able to copy human undertakings to carry out order-build jobs.
Application examination confirms that a software is free of bugs, malfunctions,
or any other flaws so that it put forward the client with an ultimate outcome.
The Future of application evaluation in 2021
Numerous of the automation mechanisms are developed to build an application examination more methodical, superior and error free apps in IT industry. In that one of the incomparable automation tool is Robotic Process Automation (RPA), is the one aforesaid technology that has automated processes in various domains over the decades. With the advantage it put forward and looks forward to discover more extensive raise in the upcoming genereations.
Functioning of RPA Build System Steps
It defines a sequence of steps for an operation to be carry out by a bot. The process is transformed into the application with the help of coding. The bot performs these steps for a perticular operation.
Benefits of RPA in an Application Testing

Robotic Process Automation not only supports a web application based, legacy, desktop free Web Content, but also mobile application since it is platform-independent. It limits begin to finalize testing by arranging and teaming up the APIs.
It empowers fulfilling the current user requires for developing faster and finer yields. RPA in application assesment
decrease inaccuracy and develops top-quality outcomes with slightest efforts. Coding capabilities are not required by groups for RPA based assesments. The programs carried out can be reutilized. It helps out bring quickness beyond functions and industry standards. RPA accelerates various software assesments. It decreases human errors and flaws, encountered in uninterrupted manual or automation assesment. RPA settles the difficulties in critical test automation.

Are Offshore Development Centers (ODCs) best for businesses and organizations?
Offshore Development Center (ODC) a helping hand to upgrade effectiveness and shrink an application development project’s functioning cost.
The replica of the Offshore Development Center is formed on the one and the same model of offshore outsourcing. It is a trade engagement prototype including dedicated and robust team to task with the client and their team to enhance and multiply their frequency range in terms of expertise, experience, gratification, and all assets.
Offshore Development Center (ODC) is rocketing universally as the global IT and application development trade. This helps out to enhance productivity and lessen an application development project’s functioning cost.
ODC outsourcing from bootstrap to large organization, has turned out to be a principal division of organizations. The ODC business prototype team runs in steady, strong and self-standing positions at the service provider’s site.
The ticket to triumph with an Offshore Development Center is that you build a continuous efforts to construct a sufficient amount of compatibility with your Offshore Development Center teams, You can give them clear commands and judge their productivity at regular intermissions. Our team at MetaProton® Technologies helps you out in performing this and lot more!
MetaProton® Technologies has been providing wide range of Computer science, development and IT services focused on the Offshore Development Center (ODC) business model with an well-established track record.
Integration testing and the best practices.
Each business nowadays wants an excellent software that conduct well and delivers an ultimate experience to its user. Then, to make sure this, these apps, softwares and web-apps are end-to-end examined to decide the accuracy of their performance, security, soundness, etc. In-between these software testing types, integration testing is carried out, afterwards the unit analysis as it validate the integration of software part.
Integration testing? what the term means.

The process of software examination technique where every single component or units of code are examined to confirm interactivity between different software system sectors. In the process of this examination, the system modules are either examined as a single class or organized iteratively. The main target of this examination is to confirm that all the units of the software work fine after blending them.
Why are the different approaches to integration testing?
The mentioned methods are different testing methods that can be followed to perform this test:
Incremental testing
This perspective includes examining minimum of two connected modules. The modules are blended and examined to pull off correct operation.
Big bang integration testing
This is the testing in which almost all of the units or major units are blended and examined in one-go.
Hybrid testing
This is the compound of the top-down and bottom-up examination.
Top-down testing
This examination includes evaluation of principal unit levels first and then shifting to bottom unit levels.
Bottom-up testing
In this testing bottom unit levels are examined first and then principal levels are examined.
The best methods of integration testing are as follows:
(1) Maintain unconnected test suites.
Integration tests shouldn't be run in conjuction with unit tests. By keeping test suites apart programmers can run unit tests at the time of development and before executing the code.
(2) Loging broadly.
Unit tests have very finite scope and examines very little pieces of the software code, thus, it is very uncomplicated to figure out the cause if the test breaks down, stops or fails. But integration test is quite complicated and dissimilar and its scope may stretch several application modules, thus it needs complete logging to examine the errors and to figure out basic issues.
(3) Conducting integration test after unit test.
In unit testing every single units of the application are examined under shield. Once the units are examined, these units are connected and tested to make sure correct integration, As a result this test has to be carried out after the finalization of the unit test.
(4) Not to examine business logic with integration test.
Integration testings take additional time as contrast to unit tests. Thus it is preferable to perform unit test for examining the business logic as unit test inspects the elementary level accuracy of code.
(5) Integration testing is not the last stop.
It is necessary to not just finish at integration testing, fairly move far off it. As the application will be deployed in an absolute production ecosystem that may contain mail servers, virtualization tools, DNS servers, databases, load balancers, proxy servers, and lot other things. Thus it is foremost step to examine all these piece and bits and to make sure that the system perfectly effect the production environment.
OutCome:
Businesses all across the world desire to execute quality standard applications that fulfil their client to fullest. To achieve this businesses verify that before their software applications are released to the market to sell, they are examined with the foremost software testing methods. To do so, businesses follow integration testing which is the most principal stage in the application development industry. But, there are definite best practices as quoted in this article that should be kept in mind while conducting this examination.

How Artificial Intelligence impacted on the Manufacturing Industry?
Artificial intelligence, the technology refers to smart machines, which the ability of human-like but robotic intelligence and carry out tasks that would generally necessitate human entanglement, it has relish quite a bit of vogue on the planet off behind time. Don’t get us wrong — all of it is indeed empowered. Goes as far, that it is now hard to think of an industry which is not using artificial intelligence to its benefit. Even a widely in manual sector such as manufacturing or service it has also found an outstanding use for it. The conventionally technology-forward industry has been so enthusiastic about artificial intelligence that experts believe its share in the manufacturing to service industry it will grow upto $20 billion by 2027 from a meager $1 billion in the beginning of 2019.
Staggering potential, isn’t it? But at the risk of sounding repetitive — none of this is without reason. Some top researchers's recent study believes that by 2033, artificial intelligence-driven tools and solutions will help companies achieve a 45 percent grow in employee potency. In the environment of the service or manufacturing sector, this would mean lessen design times, automation of quality control, better quality benchmark, and so lot more.
Let’s magnify and make it easy to understand by enlarging at some of the other advantages the manufacturing stands to profit with AI.
(1) Enhanced and better quality assurance

To be sure, crown quality remains an influential concern for manufacturing and service sectors. This forthright focuses on quality control, a second part of functioning that AI can help with. With the backing-up from data, images, materials and other relevant input, Artificial Intelligence can recognize patterns, even the most tiny defects and faults, and lot such factors that
strike the product’s standard, grade andqualities. AI can also help to clear why these quality issues are occurring and what can be done more to label said matter.
(2) Foretelling maintenance

As we know that machine downtime can cost manufacturing companies across the planet more than $450 billion every year? There is always a great demand for greater maintenance of machines, which can be bring about via Artificial Intelligence driven fortelling maintenance. It means that companies can determine exactly which device require service & maintenance
and when. It engages to examine machine sensor data, data about the weather, maintenance records, and lot more to figure out when the machine will needs service.
(3) Greater supply chain

Still one more critical aspect of a manufacturing company is the supply chain. Absolutely, Artificial Intelligence can help with that also, giving authorization to companies to guarantee optimal supply chain management, sales volumes forecast, risk management, and more. The understanding gained from the close examination of data from all practical
sources which grant companies to enhance their supply chain as stated to the market demand and polished business master plans.
The Point
Now it is plain to see that AI has lot more to offer to this industry in particular. And suppose you too want to take benefit of this AI technology. In this instance, we suggest you to discover a right-handed and reliable technology associate and stand-up with your custom software development project straight away.

What type of web hosting do I need? Client question
Nowadays a website development is much uncomplicated than it was not so long ago. Before we start developing a website some basic knowledge is necessary. The two things are going to be required before the website deployment on the web. First is the website domain (website name) and second is the hosting company where the website files will be stored to host.
When you are in the process of selecting which of the web-hosting service options are preferable for you, it might be a little bewildering. You might see a lot of terms, which might make you difficult to figure out the differences between the catagory of many web-hosting service alternatives. Some of the most types of web hosting are shared or beginner, cloud, VPS and dedicated.
(1) Shared or Beginner Hosting
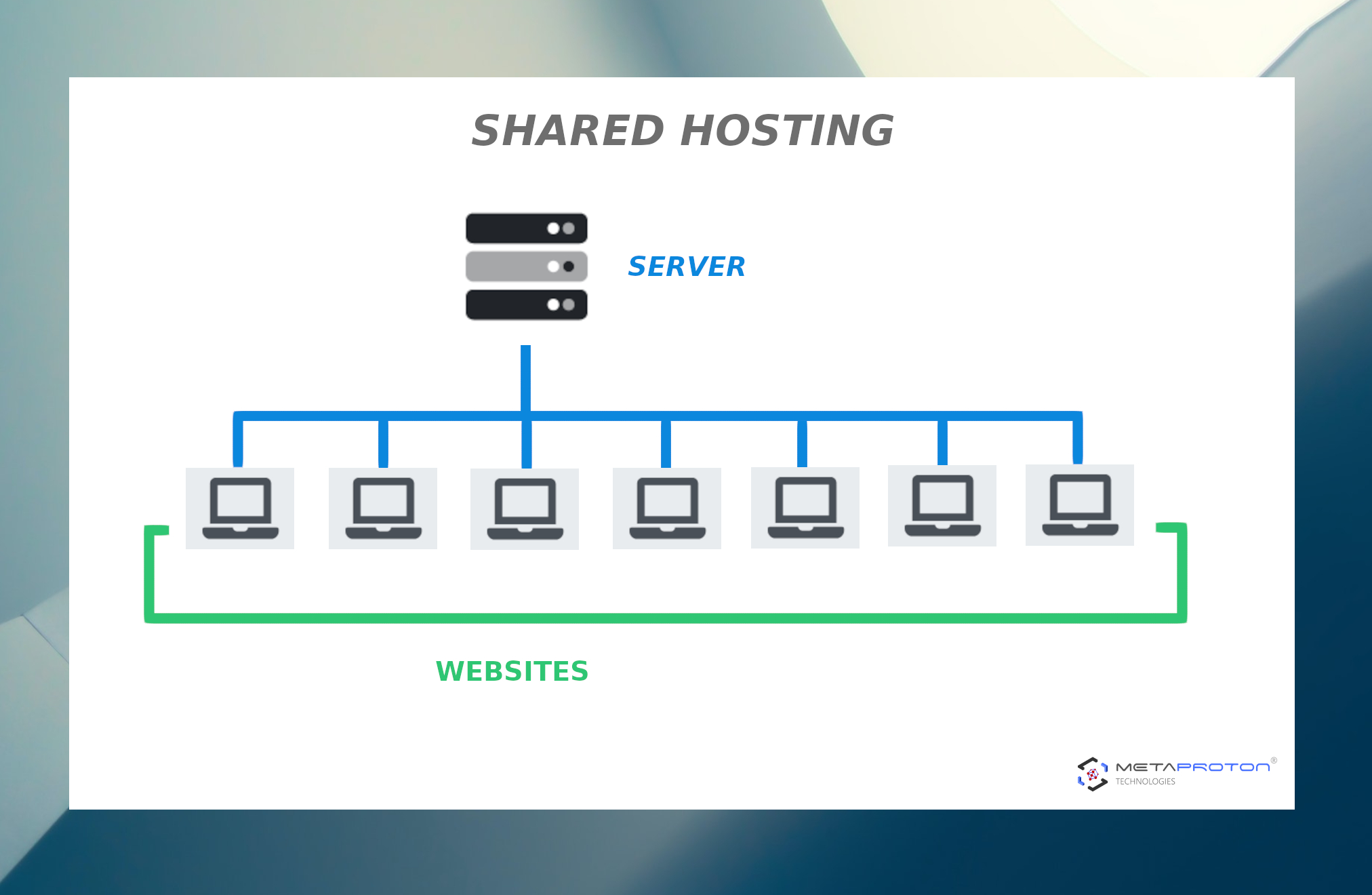
Shared or Beginner hosting plans are commonlly the most in-budget and low-cost types of web-hosting. This type of web-hosting has basic options and comes with some limitations. Since the main investment of web-hosting companies is in their servers, the shared or beginner hosting plans will allow your site to use a server space between other sites. Shared hosting plans
are suggested for simple sites, single project, small budget and beginners for initail experiments or for beginners to gain expertise and experience. So, the charge for maintaining the server is divided by the other different websites hosted there.
(2) Cloud Hosting
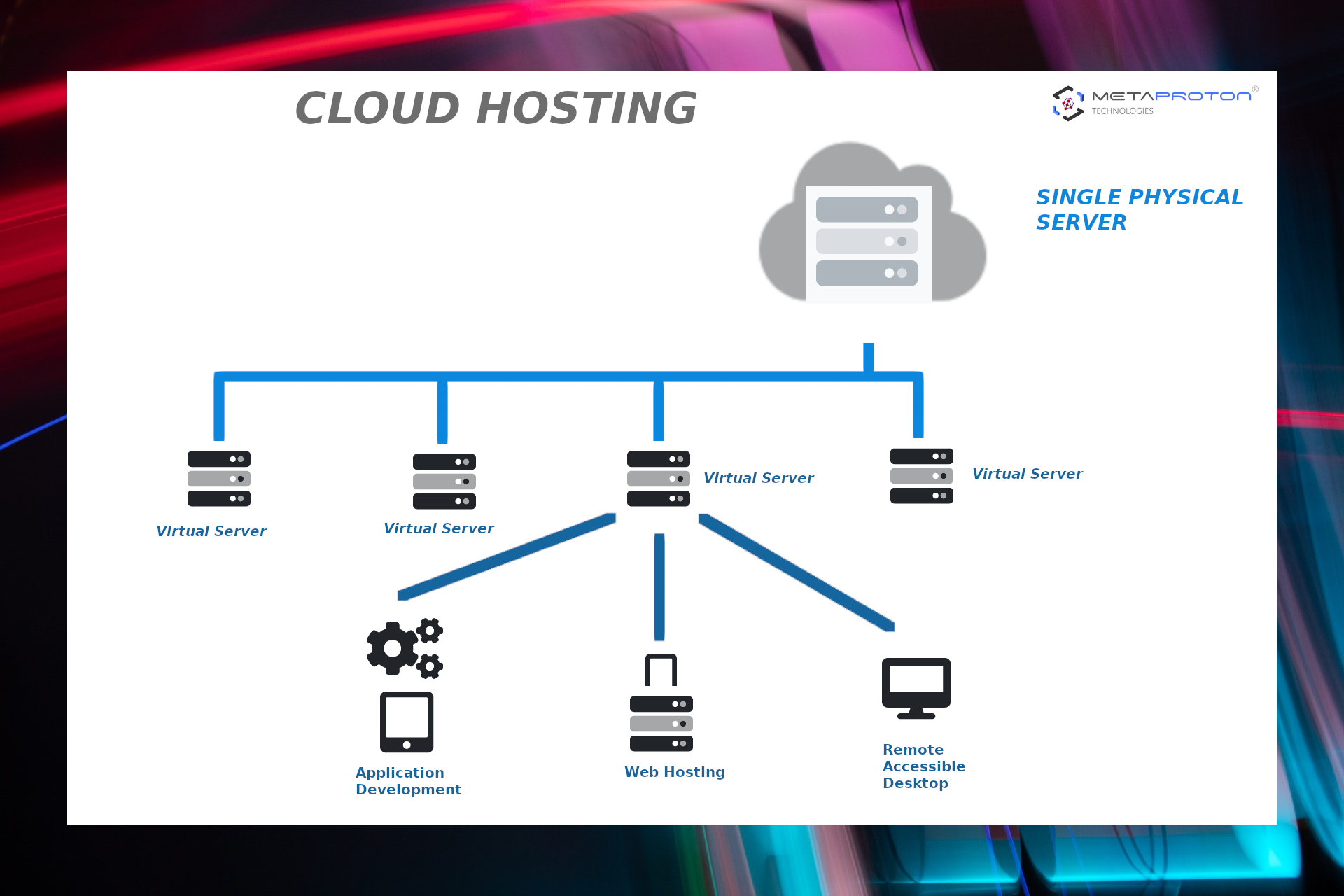
Cloud hosting technology works with a little bit different way. In this hosting various linked servers together make a cloud. So the website files are not stored on a physical server and as a result, will not only depend on it. Cloud hosting technology provides more storage space and power to the web-sites and applcations. In case one of the server is down and require time to repair,
or reboot your site will not be affected. So it doesn't mean that you have to be an master in cloud hosting technology to use it, the only thing that you must need to know is that costs more and the benefits of which are more speed, space, bandwidth, etc.
(3) VPS Hosting
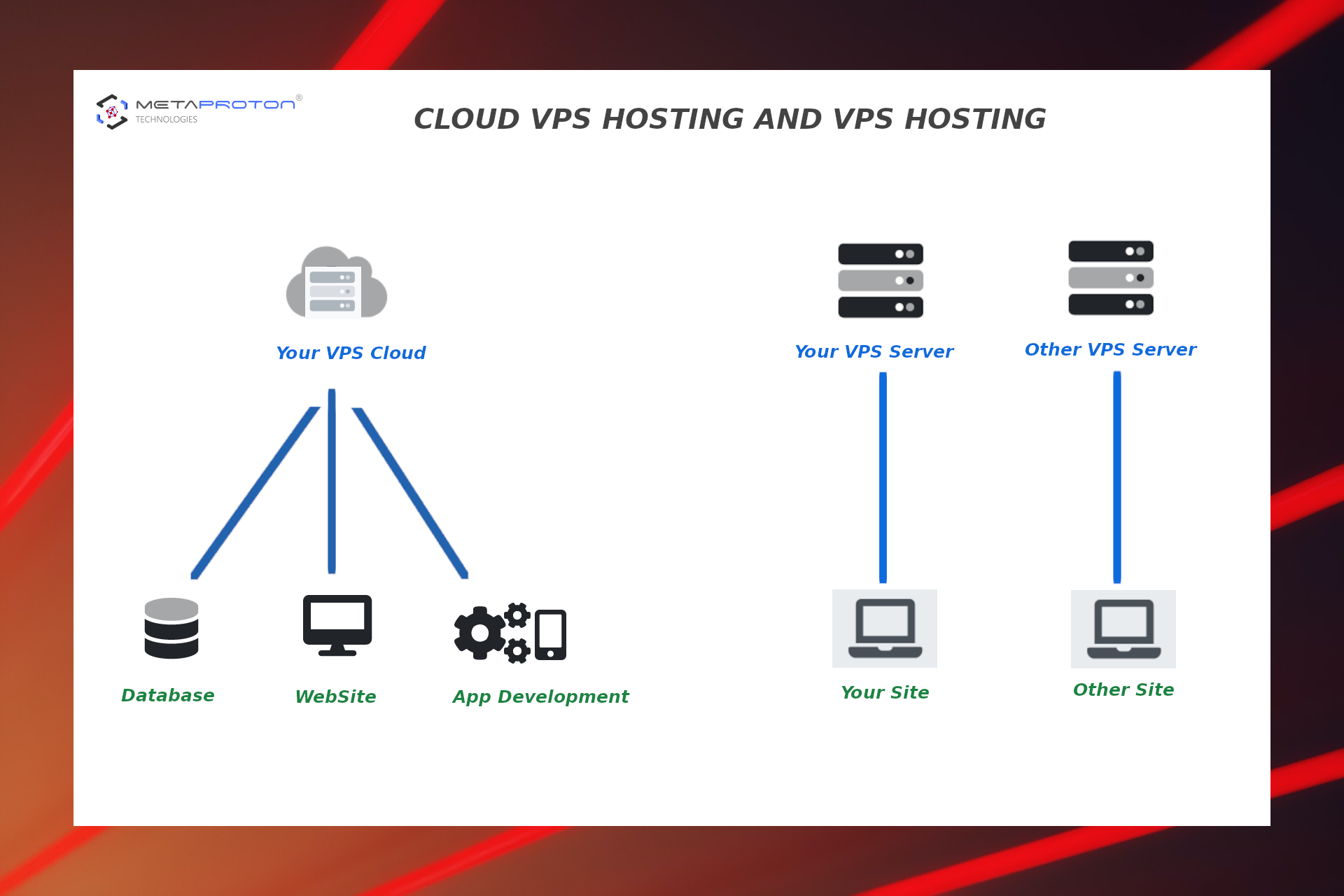
VPS or Virtual Private Server hosting is little bit similar to shared hosting. Only that you will not share a server with other websites. Having a this server comes with some benefits like you do not have to worry about how much traffic is the other sites using. In few cases, you do not have to pay for all the server space but only for what you are using. This option is chosen in most cases from
users who want to upgrade from shared hosting plans. It's appropriate for those who want to make a website for a well known brand or an e-commerce project.
(4) Dedicated Server Hosting

Dedicated Server Hosting is the case when your website and other projests will use the full storage space of a web-server. This is the topmost you can get from web hosting companies. It is used by many big company sites which get a lot of traffic, and get the maximum speed, uptime, and security. you can buy and maintain it on your own Technically if you want a server. But many
hosting companies have more temperature-controlled warehouse to keep their server in good working environment. Dedicated server hosting is the most expensive since you are not sharing the space and the costs with other sites.

Why you need a professional web content development services.
As every body aware of, content is the crown of website more than ever, so the professional web content creation and development company can help you to reach your certain requirements and demand.
Many of the business owners and entrepreneurs will obviously think about why should stop and explore website depends upon what content they have published on it. This is all about who you are what product or service you provide, how original and authentic you are about your business, how much you take care for your clients and how effective you are as a service provider or a businessmanin the industry.
As we all know, information is everything in the digital world. Content is the head of state and its quality has now become necessary than it was ever before. all might not have professionals or resources in house to manage your content requires. Browsers and search engines searches for what is real, valuable, marketable and fascinating.
The Content creators, content creating companies are not only about writing the wanted number of content hallmark but also They’re beyond that. Creators are about compute what to develop, when to develop and where it should be issued or broadcast, Content developers can get it finalized under the set down time and at discounted price.
What is "RCE" Remote Code Execution, The latest attack exploit CVE-2019-5786
Google has been alerted that a zero-day Remote Code Execution “RCE” or Arbitrary code execution "ACE" vulnerability is actively exploited by attackers to target Google Chrome users. The latest attacks exploit CVE-2019-5786, a security flaw and the only patch included in the Chrome 72.0.3626.121 version, released on March 1, 2019...
In cyber security, Remote Code Execution (RCE) or arbitrary code execution (ACE) is a method in which the attacker's ability to execute arbitrary commands or code on a target system or in a target process. A remote code execution vulnerability is a security flaw in an application or hardware allowing arbitrary code execution. The lines of code that is designed to exploit such a vulnerability is called an Remote code execution exploit. The ability to trigger arbitrary code execution over a network is often known as remote code execution (RCE).
What is the solution?
Always update and upgrade your internet browsers across your organization can be right solution.
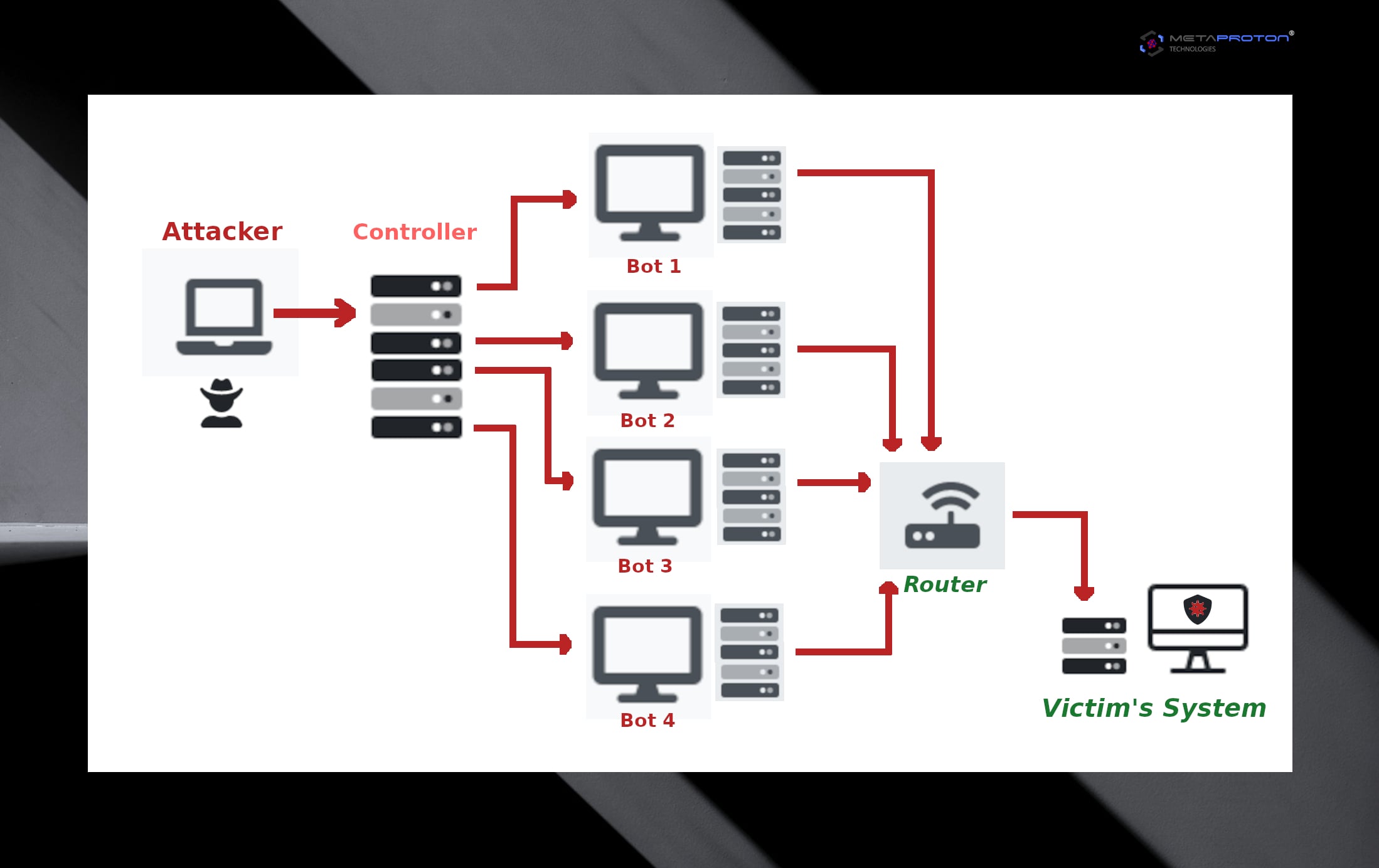
Denial-of-service attack (DoS attack or DDoS attack)
In computer technology, the denial-of-service attack (DoS attack) is a type of cyber-attack in which the perpetrator seeks to turn a machine or a network resource unreachable or unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to the Internet. DoS is typically accomplished by flooding the targeted machine, server or resource with superfluous requests in a single attempt to overload that system and prevent all legitimate requests from being fulfilled.
The distributed denial-of-service (DDoS) is large-scale DoS attack in which the perpetrator uses more than one different IP address or machines, often from ton of hosts can be infected with malware. A DDoS attack typically involves more than around 4–8 nodes on different networks fewer nodes might qualify as a DoS attack.
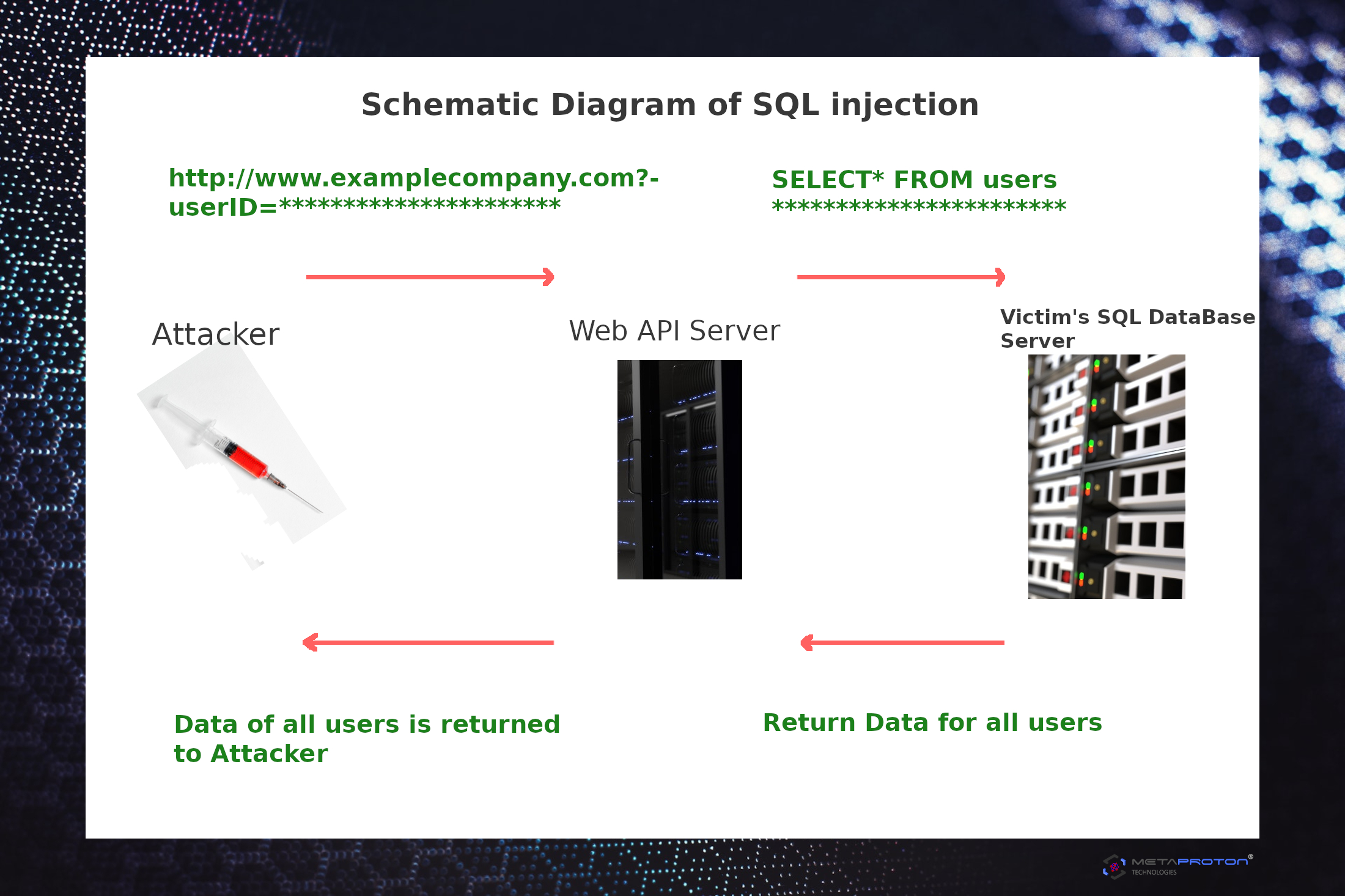
SQL injection & how to prevent that.
SQL injection is a script or code injection method, it is used to attack databases and data-driven applications, in which malicious SQL codes or statements are inserted into contact form entry field or any back-end entry field for execution. SQL injection could exploit a security vulnerability in web application's software, Eg: when user input is either filtered incorrectly for string literal escape characters wich are embedded in SQL statements or user's input is not strongly typed and unexpectedly executed.
SQL injection is well known as the attack vector for a website or web-application but it can be used to attack any type of SQL databases. This type of attacks can allow attackers to spoof identity, cause repudiation issues such as to void transactions and changing balances, it could allow the complete disclosure of the entire data on the system, destroy the data or make it unavailable, and attacker could become administrator of the database server.
How to prevent your database from SQL injection.
ANSWER: Do not use administrator level privilege to login your database account, unless if there are some compelling reason to do so. Use of a limited access to the account is much safer, and can limit what the attacker is able to do. Eg: the script or code behind a page from where you login should query the database using an account limited only to the relevant credentials table. This method, a breach through this line can not leveraged to compromise the entire database.
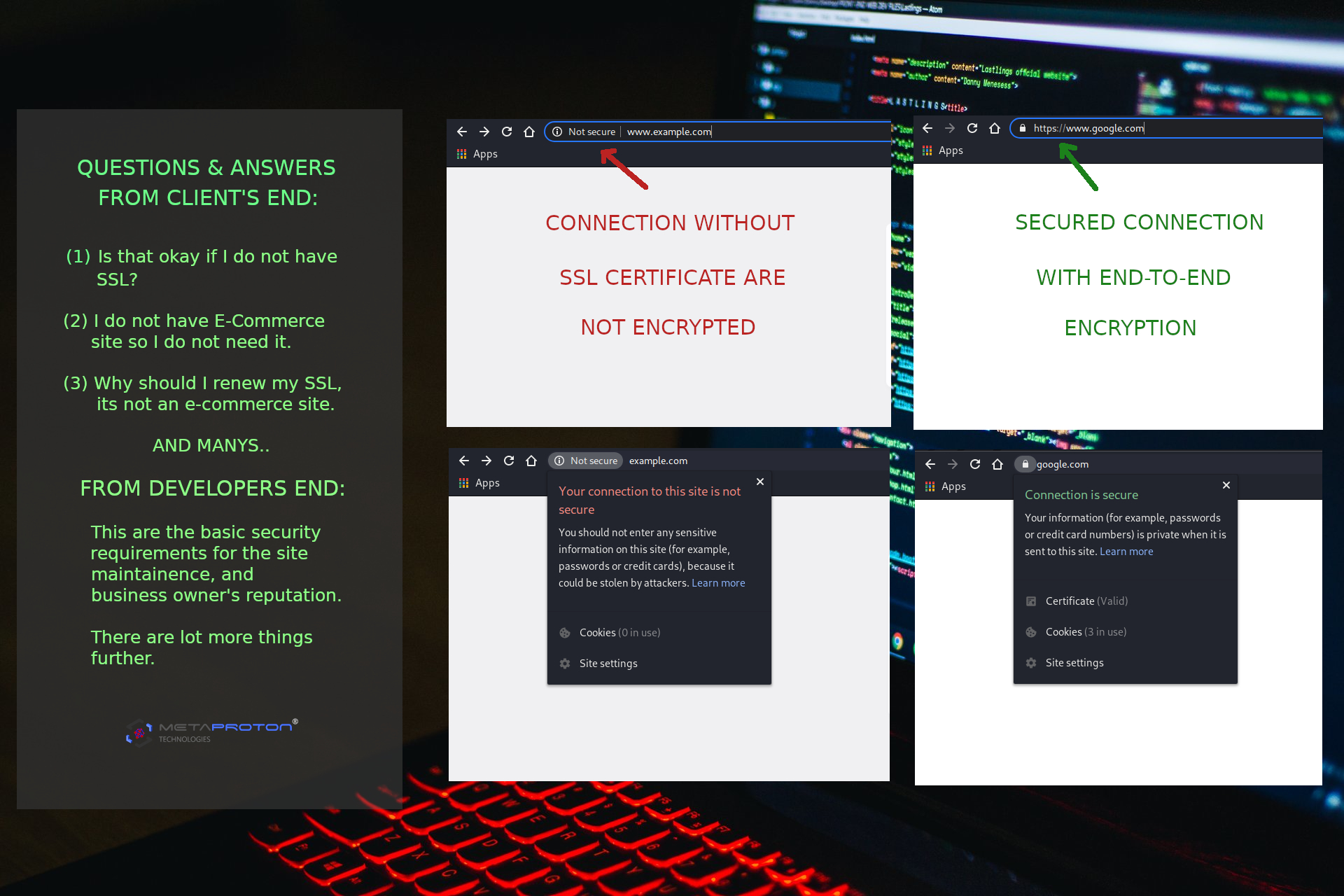
SSL certificate & why should We need that.
Any organization must install the SSL Certificate onto their web server to initiate a secure connection with the browsers. Once the secure session is established, all web traffic in between the web server and the web browser will be secure. SSL Certificate is a small data file that can digitally bind a cryptographic key with the organization’s details. When it is installed on any web server, it activates the padlock and the https protocol and allows secure connections from a web server to a browser.
Typically, SSL is used to secure credit card transactions, data transfer and logins, and more recently is becoming the norm when securing browsing of social media sites. Without SSL certificate your web-domain link looks "http://www.website.com, after integrating SSL certificate it will be https://www.website.com, the letter 's' after http stands for secured."
Why do I, any Company, Organization or any individual needs SSL certificate?
ANSWER: SSL Certificate protect their sensitive and personal information such as credit card information, usernames, passwords etc. It will not only increase Google rankings or keeping your data secure between servers but also it enhences and builts your customer's and website audience's trust with you.
Enterprise
- Automotive
- Social
- Healthcare
Developer
- Developer Network
- MetaProton Developer
Company
- Careers
- About MetaProton